A good design and approach to Cognos security can really help make your life easier. A well run and efficient model can make a software license audit a breeze, and can make day to day administration a task you don’t even notice. We have helped many clients implement security in Cognos and this is what we have learned.
In Brief.
The essential purposes and functions of security within the Cognos environment are to:
- Authenticate users to provide secure access to the BI environment,
- Provision users with appropriate capabilities and comply with software license,
- Provide secure access to content like reports and dashboards, and
- Limit access only to authorized data.
Cognos is designed to deliver these functions through:
- Integration with common authentication providers like Microsoft Active Directory Services (and many others),
- Built in groups based on licensed capabilities,
- A portal based on a file/directory paradigm that supports secured access to content, and
- A metadata model that supports the integration and mapping of security groups to data filters.
Understanding these functions and features and incorporating them into a security framework that meets business requirements will help to:
- Simplify adding, changing and removing users and managing access to content,
- Ensure license compliance and simplify potential audits,
- Provide an interface that only contains relevant content, and capabilities,
- Establish a pattern for designing and developing ongoing projects, and
- Support the development of standard content that can be deployed to wider audiences.
This will result in a Cognos implementation that performs well, is simple and intuitive to use for a variety of user profiles, and as a result maximizes user adoption and is easier to administer and maintain.
Authentication.
Cognos is easily configured to integrate with common authentication providers like Microsoft Active Directory Services. This provides the ability to use existing infrastructure to authenticate users and provide secure access to the analytics environment. Users do not need to manage additional credentials or passwords.
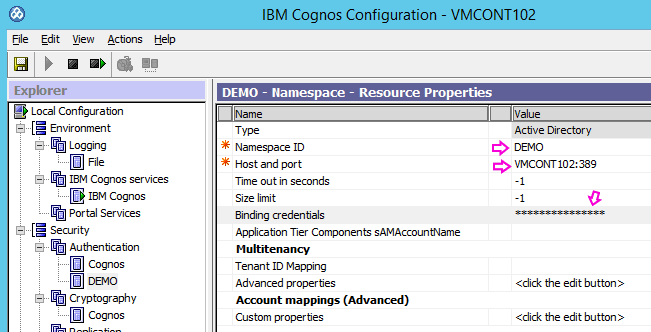
This also simplifies adding, changing and removing users and managing access to content, because it facilitates integration with existing procedures for provisioning and removing users. Cognos can also be configured with the single sign on option so that users who are already authenticated against this directory will not be prompted for credentials and, built in maintenance tasks can be used to remove content created by employees who no longer have access to keep Cognos performing as efficiently as possible.
Capabilities.
Cognos has an internal namespace that contains built in roles based on licensed capabilities. Using these roles helps simplify the process of assigning capabilities to users. This also helps to ensure license compliance and streamline potential future audits. Examples of these capabilities are Consumers, Report Authors, and Query users.
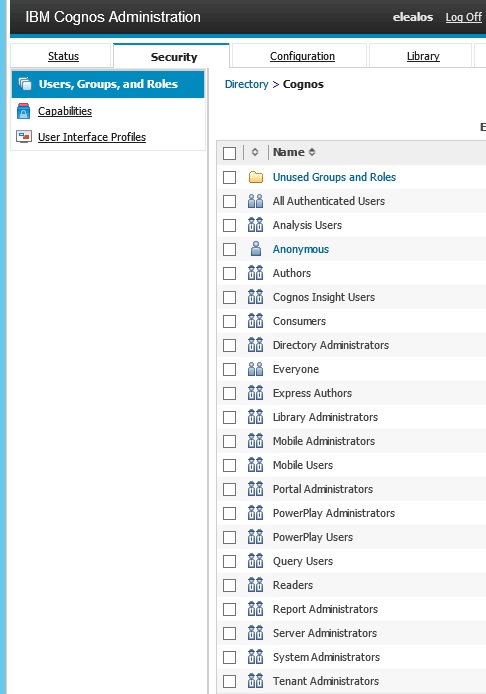
For example, if a user is assigned a Consumer group/role, the user can access Cognos and interact with BI content in the portal. If a user is assigned to the Authors group/role, the user can also create reports. These groups correspond to Cognos license levels and simplify the task of administering and compliance with license agreements. The best practice is to create relevant groups in Active Directory and assign the Active Directory Groups the corresponding roles in the Cognos namespace. This allows you to integrate the assignment of capabilities in Cognos with the standard process of provisioning users performed by the Information Security team.
Secure and Organize content.
Cognos Analytics is a portal based on a file/directory paradigm that supports secured access to folders and content, including reports and dashboards. This simplifies the user interface and helps users by only presenting relevant content, and capabilities.
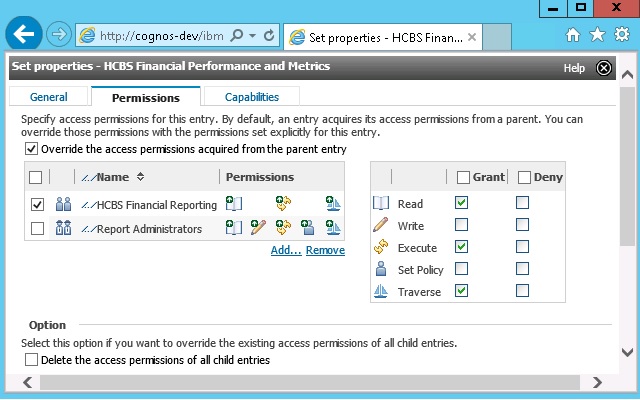
Functional based groups are groups based on logical groupings of content, like reports or dashboards. These groups provide access to folders that contain content that has been organized according to their audience – for example HR, Finance, Sales or Marketing. The members of these groups will be the users with access to this content. In practice, we recommend creating these groups and managing the members in Active Directory. This allows you to integrate the assignment of capabilities in Cognos with the standard process of provisioning users performed by the Information Security team.
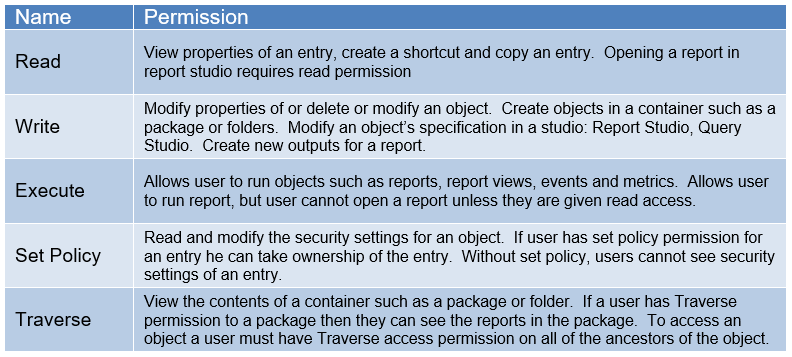
Groups can be granted different permissions, depending on their need for authorization.
Secure Data.
Cognos BI is based on a metadata model that supports the integration of security groups with data filters. This provides the functionality required to limit access only to authorized data, regardless of the content or interface being consumed by the end-user. These security groups are typically related to a dimension table in the data warehouse. The logical relationship between the security groups and the data is the basis for limiting user access and access can be limited by one, or a combination of dimensions.
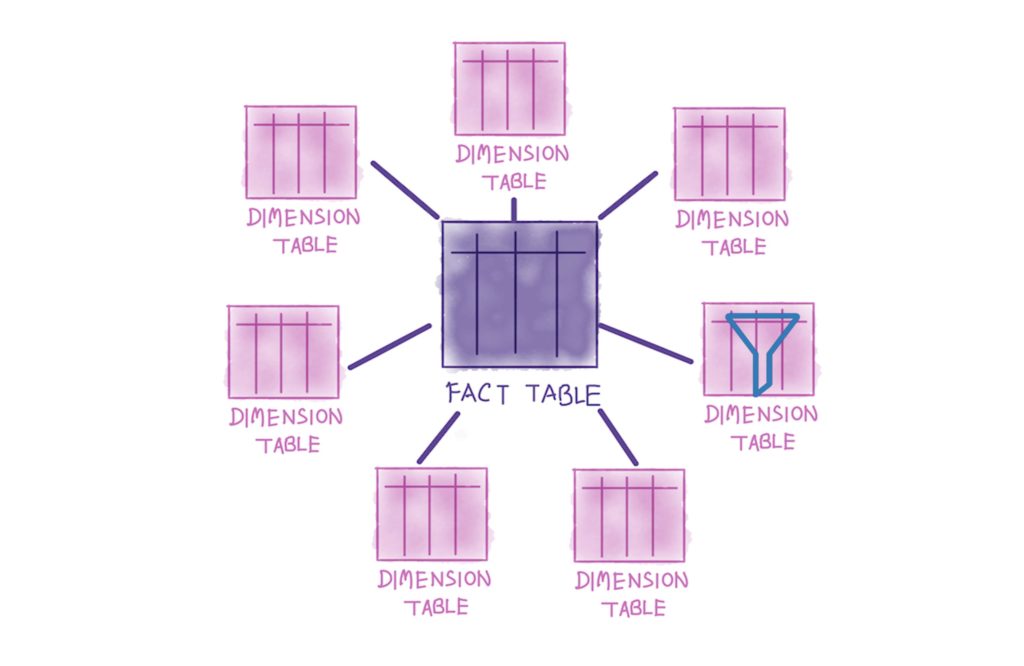
By creating security groups based on one or more dimensions, and mapping those groups to filters that limit access to data based on these dimensions, Cognos will limit data by applying a run time filter. The SQL generated to enforce the data limit is fast and efficient, and can be tuned with indexes if necessary. While this is an effective method for securing data, it has an additional benefit in that it provides an effective way to share content among users with different data needs and authorization. This makes it easier to distribute reports to a wider audience, which reduces the effort of creating and maintaining reports. because the same reports can be used by more people.
Summary
Cognos delivers essential security functions of authentication, provisioning, access and data through integratation with Active Directory Services, built in roles based on licensed capabilities, a file and directory paradigm that supports secured access to content, and a metadata model that supports the integration of security groups with data filters.
Understanding these features and incorporating them into a security framework is crucial to a successful Cognos implementation. Using the best practices outlined in this document will simplify managing users and their content, enable effective license compliance, provide an efficient user interface, establish a pattern for deploying ongoing projects, and support the development of standard content that can be deployed to wider audiences.
This will result in a Cognos implementation that performs well, is intuitive to use, maximizes user adoption and is easier to develop, deploy, administer and maintain.
I’d love to hear what you think, or have done differently. Drop me a note at elealos@quantifiedmechanix.com

